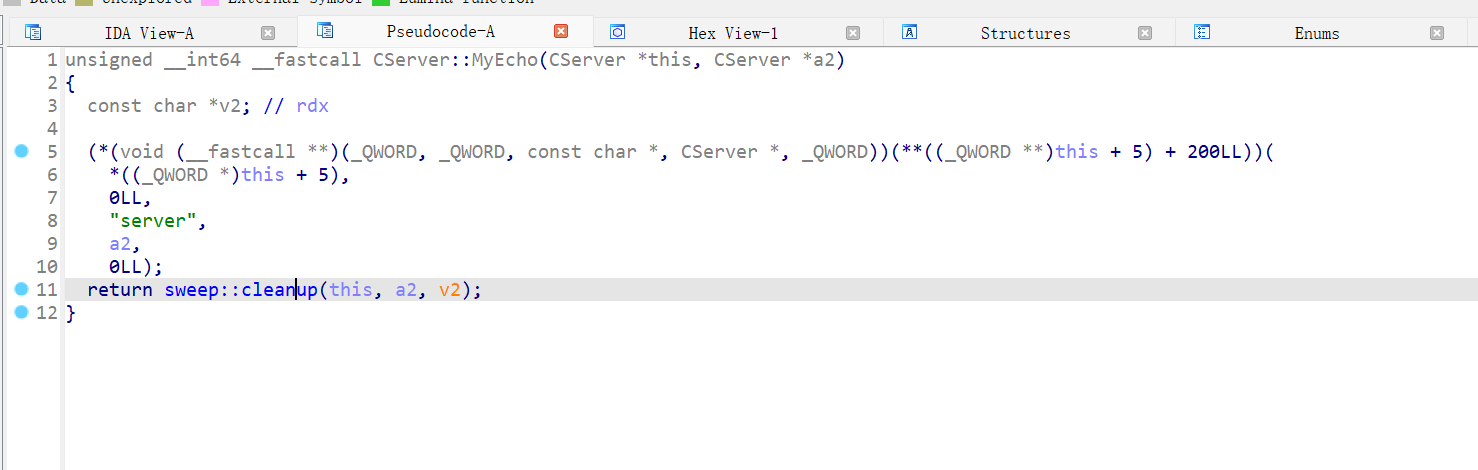
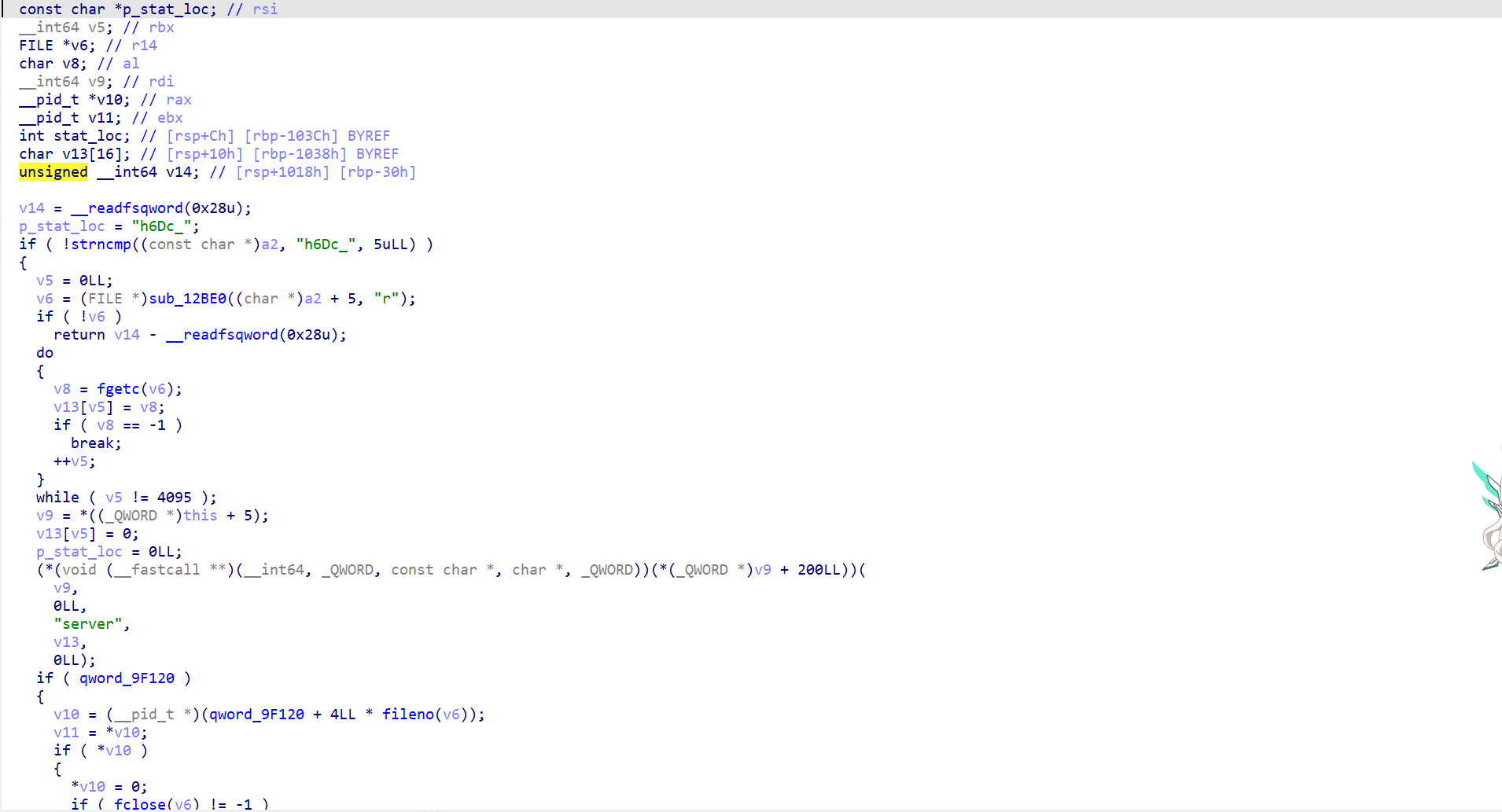
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
| def swap(a, b):
return b, a
str1 = list("flag{123aaaaavaaaaahabhhhhaaaaaaaaajaaaaaaaa456}")
list1 = [0x40, 0x3F, 0x31, 0x94, 0x69, 0x3E, 0x9C, 0xA3,0x60, 0x9B, 0x5B, 0x56, 0x70, 0x24, 0x87, 0x17,0x68, 0xCA, 0x97, 0xBA, 0xAA, 0x18, 0xA9, 0x11,0xB0, 0xD3, 0x3D, 0x9B, 0xAB, 0xB0, 0xF1, 0xB8,0xE4, 0x35, 0x18, 0x6A, 0xFB, 0x49, 0x87, 0x48,0x58, 0x81, 0xE9, 0x8F, 0xF7, 0x26, 0x29, 0x08]
for i in range(0, 48, 8):
str1[i], str1[i+5] = swap(str1[i], str1[i+5])
str1[i+1], str1[i+7] = swap(str1[i+1], str1[i+7])
str1[i+2], str1[i+6] = swap(str1[i+2], str1[i+6])
for j in range(0, 8):
str1[i+j] = chr((ord(str1[i+j]) - i - j))
str1[i+3], str1[i+4] = swap(str1[i+3], str1[i+4])
print(''.join(str1))
print(''.join([chr(ord(i) ^ 0x28 )for i in str1]))
print([hex(ord(i) ^ 0x28) for i in str1])
print([hex(((ord(str1[i]) ^ 0x28) + list1[i])& 0xff) for i in range(0,48)])
print([((ord(str1[i]) ^ 0x28) + list1[i])& 0xff for i in range(0,48)])
list2 = [0x9C, 0x56, 0x89, 0xF3, 0xB5, 0x87, 0x0F, 0xF0, 0xD1, 0x9B, 0x6C, 0xA4, 0xD1, 0xA2, 0x00, 0x35, 0x81, 0xD4, 0xB0, 0x30, 0xF3, 0x89, 0x0A, 0x89, 0x13, 0x45, 0xA0, 0x08, 0xCA, 0x1F, 0x0F, 0x20, 0x00, 0x4F, 0x56, 0x81, 0x03, 0x5B, 0xAB, 0xC3, 0xC7, 0xFD, 0x57, 0xBB, 0x09, 0x3B, 0x95, 0x08]
for i in range(0,48) :
list2[i] = ((list2[i] - list1[i]) ^0x28)& 0xff
for i in range(0, 48, 8):
list2[i+3], list2[i+4] = swap(list2[i+3], list2[i+4])
for j in range(0, 8):
list2[i+j] = list2[i+j] + i + j
list2[i+2], list2[i+6] = swap(list2[i+2], list2[i+6])
list2[i+1], list2[i+7] = swap(list2[i+1], list2[i+7])
list2[i], list2[i+5] = swap(list2[i], list2[i+5])
print(''.join([chr(i &0xff)for i in list2]))
|